Configuring Your Firewall (Continued)
UPNP
If there's one thing I'd like people to do on their firewall is to disable UPNP. Although UPNP removes the hassle of opening up ports, there are many ways for people to take advantage of UPNP to penetrate your firewall.
Why is UPNP so vulnerable to such threats? Well, UPNP was originally devised to allow total newbies to set up network by allowing devices to communicate with each other with nearly no input from the user. Unfortunately, an attacker can take advantage of this open system by spoofing the UPNP system to gain access to the network. Ouch.
Change The Password
Most users may not know this - routers can be easily accessed from the Internet. The router itself is generally impenetrable, unless someone knows the password to the router. But that's a no-brainer if you just leave the router's default password as it is.
If you do not change the router's password, anyone with the ability to use SSH or Telnet can literally remotely administrate your router. Ouch! Don't want that to happen? Change your router password ASAP!
Read The Log
We may consider firewall logs to be the purveyors of pointless details most of the time. But they can actually work like the manual methods I described in the earlier section and help you hunt down potential mischief makers.
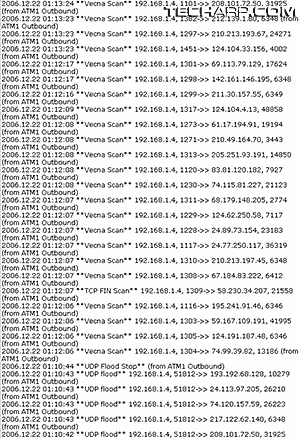 |
For example, my sister recently complained that her PC would keep disconnecting itself from the Internet after just two hours of use. I was really perplexed, so I check her PC and found nothing obviously wrong.
So I ran through the firewall log and noted the following results (see picture on the right).
Doesn't seem too interesting, right? But if you scan through it, you will notice one thing - that something using those ports has been beating the outgoing connection to the Internet with tons of packets.
After doing a quick search on the programs using those ports, I finally hunted down the offending software and wiped it off the PC.
This serves as a point on how logs may be boring, but they're incredibly useful since it lists down details on practically every change or port use in the router.
Ever wondered why you can't use a certain program because it can't connect to the Internet? Ever wonder why your ping time is high? Ever wonder why your downloads have suddenly become insufferably slow? Do yourself a favour. Check the router logs and you might find out a thing or two.
I guess that's all for the firewall section, There isn't much to it, is there? Yeah, it's pretty simple because the hardware pretty much takes care of the hunting. Of course, port forwarding could be a real headache at first, but you will get the hang of it after a few times.
<<< Configuring Your Firewall, MAC Filtering : Previous Page | Next Page : Patching Up The Holes, Tier 0 : Firmware Or Hardware >>>






 Add to Reddit
Add to Reddit
