Advanced Spyware Diagnosis
Process Scanner
 |
 |
If you feel that the simple, one-click scan and remove option in most spyware scanners are below you and would like to try something more advanced diagnostics, try this software - Process Scanner.
This software takes the guesswork out of diagnosing your operating system's running processes. Plus, it comes with a really nifty interface!
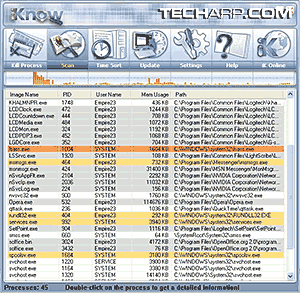
Like all other diagnostic software, it has an update feature you should use regularly. If you see a process is highlighted, the risk of it being spyware is high. Of course, you could argue from the picture on the right that a lot of harmless Windows XP services are also highlighted. But this is to be expected, as spyware often masquerades as these essential processes.
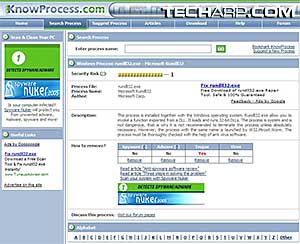
So, don't just kill a process because it's highlighted by Process Scanner in color. Double-click and get detailed information on it to diagnose a potentially harmful process. The way Process Scanner puts it, it's pretty easy to understand. Simple enough even for newbies to understand and decide on whether they should investigate further and/or kill the process.
It is extremely helpful when it comes to hunting spyware baddies hiding inside your PC. Just avoid being trigger-happy and kill an essential process. That can crash your operating system. Think of this tool as an easy way to check and snoop around your operating system's list of processes, not as a raging killing machine.
Do note that it won't mitigate the need for other forms of spyware protection. But in my view, every little bit helps. Use this tool as a supplement to your other anti-spyware software and you will be much safer.
Hijack This!
 |
 |
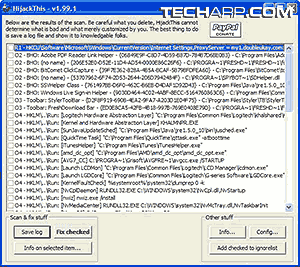
Made by a programmer called Merijn, this is quite an extreme tool to use, because it scans for everything that is different from a reference safe PC. But it has this special ability to detect and kill most forms of spyware with a brutality like no other.
However, think long and think hard before clicking that FIX button. Hijack This! is sometimes too efficient a scanner and will display all differences between your PC and a reference safe PC. Not all references are bad, of course. But how do you determine which is safe and which is bad? Well, this is where you need to do a little homework.
You need to seach online (use Google or Live) and see if the differences highlighted are normal... or something you should be wary of. If you are lucky enough to know someone who is knowledgeable about spyware, you can get him/her to help identify the questionable components. Although this might seem like a lot of work, this is work worth doing, especially if it helps you catch and kill sneaky spyware hiding in your system.
If you cannot find anyone to help you, try this :
- Click Save Log.
- Open the log file using Notepad.
- Go to a tech forum like forums.techarp.com or tomcoyote.org.
- Post your question and the log.
- Wait until the gurus reply with suggestions on which entries to be deleted.
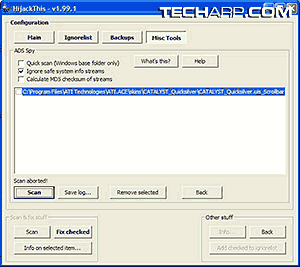
As spyware writers get smarter and more innovative about bypassing current detection methods, not even Hijack This! can guarantee a completely clean system. This is especially true when the spyware is hidden within metadata steams (e.g. EXIF data in photos). For such hardier types of spyware, Hijack This! includes a nifty little utility called ADS Spy which hunts for spyware in alternate data streams (ADS) and lists them out so that you may pick them out.
Just like the main Hijack This! software, it also lists legitimate ADSes. So, I suggest you approach an expert for suggestions on what to retain and what to remove. Use the same method outlined above. Save the log file and send it to a knowledgeable friend or post it in a tech forum.
<<< An Introduction To Spyware, Diagnosis & Removal : Previous Page | Next Page : Prevention Is Better Than Cure, Prudence >>>






 Add to Reddit
Add to Reddit
