ED#165 : Apple iOS And OS X Have A Critical Security Hole And The Fix Is Here
![]() On Friday, the 21st of February, Apple acknowledged that they had a critical security hole in their iOS operating system. It was specifically an SSL (Secure Socket Layer) vulnerability in iOS and OS X that exposes iOS and OS X devices to a "man in the middle" attack.
On Friday, the 21st of February, Apple acknowledged that they had a critical security hole in their iOS operating system. It was specifically an SSL (Secure Socket Layer) vulnerability in iOS and OS X that exposes iOS and OS X devices to a "man in the middle" attack.
Apparently, Apple used "raw OpenSSL for HTTPS, but didn't include hostname verification". This is a glaring flaw because it would allow anyone with a valid SSL certificate to masquerade as a trusted website to harvest your communications or login information.
Normally, SSL prevents that by verifying that you are communicating with the correct website, but since Apple (inadvertently) forgot to validate the hostname, it doesn't actually verify the authenticity of the website, just the validity of the SSL certificate. As long as the masquerading website has a valid SSL certificate, Apple iOS and OS X will verify it as the correct website even though the SSL certificate name does NOT match the actual hostname. As you can see, this flaw renders SSL in iOS and OS X utterly useless as an authentication process.
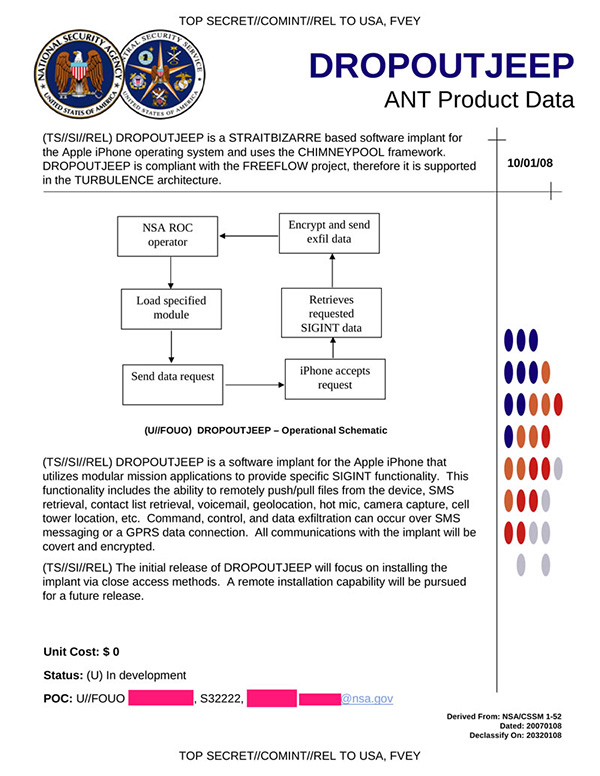
There is speculation that this could well be the security hole which the NSA exploited to insert the DROPOUTJEEP software implant, probably using automatic updates via SSL. DROPOUTJEEP, whose existence was revealed by Edward Snowden, targets the Apple iPhone (but could conceivably be used on all other iOS devices) and allows the NSA to "remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic, camera capture, cell tower location, etc. Command, control and data exfiltration can occur over SMS messaging or a GPRS data connection. All communications with the implant will be covert and encrypted.”
Backdoors Found In Bitlocker, FileVault and TrueCrypt?
Of course, this could all just be nothing more than an innocent bug, as Adam Langley pointed out yesterday :
So here's the Apple bug:
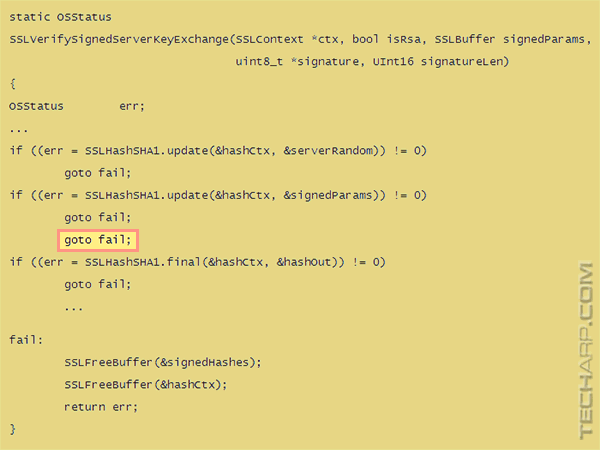
Note the two goto fail lines in a row. The first one is correctly bound to the if statement but the second, despite the indentation, isn't conditional at all. The code will always jump to the end from that second goto, err will contain a successful value because the SHA1 update operation was successful and so the signature verification will never fail.
This signature verification is checking the signature in a ServerKeyExchange message. This is used in DHE and ECDHE ciphersuites to communicate the ephemeral key for the connection. The server is saying “here's the ephemeral key and here's a signature, from my certificate, so you know that it's from me”. Now, if the link between the ephemeral key and the certificate chain is broken, then everything falls apart. It's possible to send a correct certificate chain to the client, but sign the handshake with the wrong private key, or not sign it at all! There's no proof that the server possesses the private key matching the public key in its certificate.
Since this is in SecureTransport, it affects iOS from some point prior to 7.0.6 (I confirmed on 7.0.4) and also OS X (confirmed on 10.9.1). It affects anything that uses SecureTransport, which is most software on those platforms although not Chrome and Firefox, which both use NSS for SSL/TLS. However, that doesn't mean very much if, say, the software update systems on your machine might be using SecureTransport.
However, it now appears that this bug was introduced in iOS 6.0 which debuted on 24th September 2012. In the following month, Snowden's leaked documents revealed that the NSA had successfully penetrated Apple's servers. Naturally, Apple has denied, and continues to deny, that the NSA can access or are accessing its servers or iOS devices as Snowden's leaked documents claim. Still, there is no denying that such a bug is a major flaw, and allows iOS and Mac OS to be exploited by malicious persons.
How To Fix Whatsapp Chat History Corruption
So How Do We Fix It?
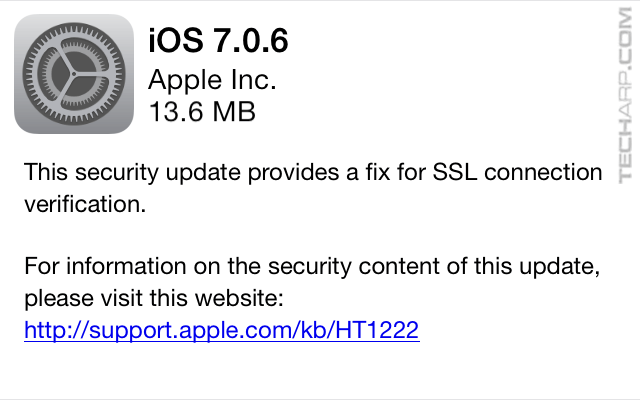
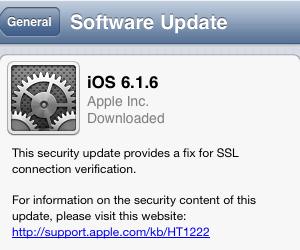
You may not have noticed it but Apple has quietly released iOS 7.0.6 and iOS 6.1.6, which specifically patches this vulnerability and restores the verification of the hostname. To update, just go to Settings -> General -> Software Update and click Download and Install. Alternatively, you can plug your iOS device to your computer and use iTunes to update it (using the Check for update button). We highly recommend you do so ASAP.
iOS 7.0.6 (build number 11b651) is available for the Phone 4 and later, iPod touch (5th generation), iPad 2 and later, and weighs in at around 13.6 MB on the iPhone 4S and 35.5 MB on the iPhone 5S.
iOS 6.1.6 (build number 10b500), on the other hand, is available for the iPhone 3GS and the iPod touch (4th generation).
 |
Since this bug was only introduced in iOS 6.0, iOS devices using older versions of iOS are safe from this vulnerability.
Java Plug-in SSV Helper - Should It Stay Or Should It Go?
What Should OS X Users Do?
This vulnerability also affects OS X, but Apple has remained mum on when a fix is expected. The good news is that it appears that this vulnerability was only introduced in OS X 10.9, so users of older versions of OS X should be safe. However, what should an OS X user who is affected do in the meantime?
This vulnerability is mostly an issue if you are on a public network, where a hacker is already on the same network as you are. You should try to abide by these rules :
-
Avoid using public networks until Apple issues a patch and you install it.
-
If you need to use a public network, you should avoid accessing any websites that require logging in. Viewing websites that do not require any login (e.g. news websites) is perfectly safe.
- If you have a Windows-based PC, use that instead to access websites that require logging in, especially your online banking accounts.
 These rules are particularly important for OS X users because the cat is out of the bag, and there's no fix. Hackers will definitely try to exploit this vulnerability while they can.
These rules are particularly important for OS X users because the cat is out of the bag, and there's no fix. Hackers will definitely try to exploit this vulnerability while they can.
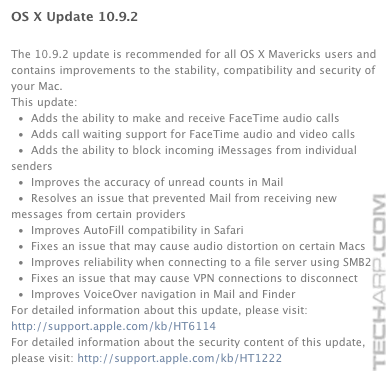
Updated @ 26/02/2014 : Five days after they announced the SSL vulnerability, Apple finally issues a fix for OS X. However, instead of informing anyone about it, they slipped the fix into the already planned OS X 10.9.2 update.
If you check the list of fixes and improvements in OS X 10.9.2 on the right, you will not see the fix listed even though it's part of the update. However, it is mentioned in the full list in the Knowledge Base - "Provides a fix for SSL connection verification".
Download the OS X 10.9.2 update and install it as soon as you can. This is a major update that weighs in at 460 MB, so it may take a while on slower connections. Once you have installed it though, you can safely access websites that use SSL to authenticate themselves.
| If you like this article, please share it! -> |
Other Scoops
- Warning - Microsoft Opened A Security Hole In Internet Explorer 11
- How To Fix Keychain Corruption In OS X Mavericks
- U Mobile Announces New Surprises For The New Year!
- AMD's Early 2014 Processor & Graphics Roadmap
- How To Fix Whatsapp Chat History Corruption
- How To Fix GDI Leaks In Internet Explorer 10 and 9
- WhatsApp Is Moving To A Subscription Model? Don't Panic!
- The NVIDIA Control Panel Memory Leak Problem
If you have a scoop you want to share with us, just contact us! It doesn't have to be Apple-related. It can be anything in the tech industry, from mobile phones to P2P software. Just drop us a message!
Support Tech ARP!
If you like our work, you can help support out work by visiting our sponsors, participate in the Tech ARP Forums, or even donate to our fund. Any help you can render is greatly appreciated!
Support us by buying from Amazon.com! |
|
| Grab a FREE 30-day trial of Amazon Prime for free shipping, instant access to 40,000 movies and TV episodes and the Kindle Owners' Lending Library! | |
Questions & Comments
If you have a question or comment on this editorial, please feel free to post them here!
Date |
Revision |
Revision History |
23-02-2014 |
1.0 |
Initial Release. |
24-02-2014 |
2.0 |
Added a new section - "What Should OS X Users Do?" |
26-02-2014 |
2.1 |
Added an update about the newly released OS X 10.9.2 update which fixes the SSL bug for OS X. |






 Add to Reddit
Add to Reddit