ED#176 : TrueCrypt Developer Drops New Bombshell - Open Source Fork "Impossible"
Sometime on the 28th of May, 2014, the anonymous developers of TrueCrypt mysteriously pulled the plug on their popular encryption software. They shut down the TrueCrypt.org website and redirected visitors to a simple page hosted by SourceForge, with a disturbing warning :
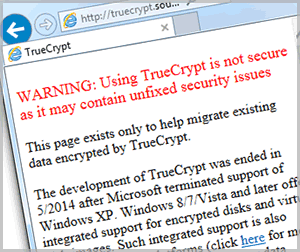
WARNING: Using TrueCrypt is not secure as it may contain unfixed security issues
This page exists only to help migrate existing data encrypted by TrueCrypt.
The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform.
That warning is then followed by instructions on how users may migrate from TrueCrypt to BitLocker. Right at the end is a link to TrueCrypt 7.2, the first update since TrueCrypt 7.1a was released in 2012. However, this version of TrueCrypt will only decrypt TrueCrypt containers - its encryption ability has been disabled / removed.
There has been much speculation about the reasons for pulling the plug. On one end, many TrueCrypt users were hoping that the website was just hacked and that the world, as they knew it, would return. On the other hand, there were conspiracy theories that the developers were being threatened by the NSA to divulge or add a backdoor, or were the NSA themselves!
Well, it's been more than 3 weeks since TrueCrypt went down, and one thing's for sure - the website was not hacked, and it was the actual intent of the mysterious developers of TrueCrypt to pull the plug. Even worse - they are now denying the world the right to "fork" TrueCrypt's development.
The Mystery Of TrueCrypt's Disappearance
| If you like this article, please share it! -> |
TrueCrypt Developer Says Open Source Fork Is "Impossible"
If you read our piece, The Mystery Of TrueCrypt's Disappearance, you would know that one of the principals of the effort to audit TrueCrypt was Matthew Green (a Cryptography Research Professor at the Johns Hopkins University).
He had prior contact with the TrueCrypt developers and reached out to them about forking its development with this email:
Hi, I hope you’re well. I understand from seeing some previous emails that you were one of the Truecrypt developers, and that you’re no longer interested in continuing work on the project. I understand and can sympathize with that. For the past several months we’ve been (very slowly) auditing the TC code. Now that you’re no longer maintaining it, there seems to be a great deal of interest in forking it. I think this interest has reached the point where a fork is virtually inevitable. This makes me somewhat worried. We think Truecrypt is an important project — no proprietary disk encryption system offers cross-platform support and the same feature set. Moreover, Truecrypt is unlikely to ‘go away’ just because the developers have abandoned the project. In fact, it may become significantly less secure if it goes forward as samizdat or as part of some unauthorized fork. We’d like the project to continue, but in a responsible way. That means fully auditing all of the crypto/container and bootloader code and (likely) replacing much of it with fresh implementations. Even though this will require some substantial re-development it still seems more practical than starting from scratch. The current plan is being led by a group of people who have a great deal of experience with cryptography and the expertise to identify flaws, but would prefer not to engineer from scratch. The main concern we have right now is with the license structure and trademarks associated with Truecrypt. Of course some will fork the reject regardless of the legal issues, but this doesn’t seem appropriate without clear guidance. What we would like is permission to take at least portions of the current codebase and fork it under a standard open source license (e.g., GPL/MIT/BSD). We would also like permission to use the Truecrypt trademark as part of this effort. If that’s not possible, we would accept a clear statement that you would prefer the software not be renamed. I realize this is a great deal to ask, but I would ask you to consider the alternative. Without expert attention there’s a high likelihood that TC 7.1a or some future insecure fork will occupy the niche that a secure version of TC could occupy. Giving your permission to undertake a responsible process of forking and redevelopment would ensure that your work can go on, and that nobody is at risk from using older software. I appreciate any consideration you could give this note. Thank you, Matt |
The developer just responded in a very short e-mail, killing all hope of an official open source fork :
I am sorry, but I think what you're asking for here is impossible. I don't feel that forking truecrypt would be a good idea, a complete rewrite was something we wanted to do for a while. I believe that starting from scratch wouldn't require much more work than actually learning and understanding all of truecrypts current codebase. |
While the developer does not mind the source code (which you can download here) being used as reference for a new open source encryption software, he/she won't agree to the forking of TrueCrypt under a standard open source license, or even the use of its trademark or name. To summarise,
-
The community must develop a brand-new encryption software from scratch to replace TrueCrypt.
-
Any developer of such a software can examine TrueCrypt's source code to learn, but they may not borrow any portion for use in the new software.
-
Neither can the developer use the TrueCrypt trademark or name.
Basically, they are not only shutting down TrueCrypt but they want to bury it permanently while giving a third finger to the community. If the community decides to embark on a replacement software, it will have to do it from scratch. Fantastic.
The Solid State Drive Optimization Guide
| If you like this article, please share it! -> |
What Should We Do?
As we said before, there's no reason to panic or start migrating to other encryption software. TrueCrypt 7.1a has worked perfectly fine for the last 2.5 years on a variety of operating systems including the very latest Windows 8.1 and OS X Mavericks so there's no reason to believe that it won't be serving us well for many years to come.
If you accidentally upgraded to TrueCrypt 7.2, or need a copy of TrueCrypt 7.1a for a different platform, you can download it from our repository. Just scroll down to the "Where Can I Still Download TrueCrypt" section.
On the other hand, the developer's refusal to allow the community to fork TrueCrypt's development would make it harder and longer for any team that takes up the challenge to replace TrueCrypt to successfully developing a viable replacement. It would likely take years before any team can develop a replacement encryption software that is good enough to replace TrueCrypt.
It may also mean that it would be impossible to "legally" patch any security holes in TrueCrypt that may be discovered from this point henceforth, although it's unlikely that the TrueCrypt developers would litigate anyone who attempts to do so anyway, as this could well expose their identities which they have tried very hard to keep anonymous.
How to add extra cloud storage services into Microsoft Office 2013
| If you like this article, please share it! -> |
Other Scoops
- How To Integrate Cloud Storage Services With Microsoft Office 2013
- The Mystery Of TrueCrypt's Disappearance
- Windows May Fail To Boot Up After Installing Latest IE Patch
- Intel Xeon "Haswell Refresh" CPU Details Leaked
- Should You Select MBR Or GPT When You Install A New Drive?
- Bitcoin Malware Infects Apple iAd!
- These Malware Could Be Using Your Smartphone To Mine Cryptocurrencies!
- How To Fix The Apple iCloud Bug (Missing Contacts)
If you have a scoop you want to share with us, just contact us! It doesn't have to be Microsoft-related. It can be anything in the tech industry, from mobile phones to P2P software. Just drop us a message!
Support Tech ARP!
If you like our work, you can help support out work by visiting our sponsors, participate in the Tech ARP Forums, or even donate to our fund. Any help you can render is greatly appreciated!
Support us by buying from Amazon.com! |
|
| Grab a FREE 30-day trial of Amazon Prime for free shipping, instant access to 40,000 movies and TV episodes and the Kindle Owners' Lending Library! | |
Questions & Comments
If you have a question or comment on this editorial, please feel free to post them here!
Date |
Revision |
Revision History |
| 20-06-2014 | 1.0 |
Initial Release. |







 Add to Reddit
Add to Reddit
