ED#169 : These Malware Could Be Using Your Smartphone To Mine Cryptocurrencies!
![]() Earlier this year, mobile security researchers discovered the presence of a new family of Android malware, which they called ANDROIDOS_KAGECOIN.HBT because of its ability to mine cryptocurrencies like Bitcoins, Dogecoins and Litecoins.
Earlier this year, mobile security researchers discovered the presence of a new family of Android malware, which they called ANDROIDOS_KAGECOIN.HBT because of its ability to mine cryptocurrencies like Bitcoins, Dogecoins and Litecoins.
What's intriguing about these malware is not only the fact that they are being used to mine cryptocurrencies, it is also the way their creator appropriated code from legitimate apps to achieve his goals.
The malware creator took the CPU mining code from Crypto Miner, a legitimate Android cryptocurrency mining app (that was itself based on the open-sourced cpuminer software), and injected it into legitimate apps like Football Manager Handheld and TuneIn Radio. This allowed the malware to appear as functional copies of the real apps, while "mining" cryptocurrencies for the malware creator.
According to Veo Zhang, a Mobile Threat Analyst from Trend Micro, they hid the malicious code by modifying the Google Mobile Ads code :
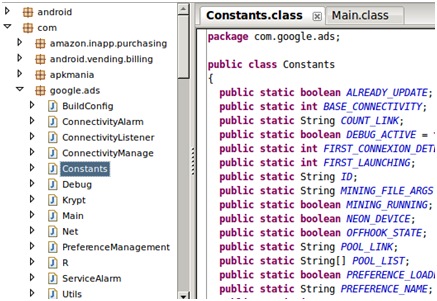
When the infected device connects to the Internet, the mining code starts up as a background service and connects to a dynamic domain (http://flow.{BLOCKED}o.me:9xxx) which redirects it to an anonymous Dogecoin mining pool. The infected apps were also configured to download a configuration file (from http://poolsaturn.{BLOCKED}h.net/update.php?p=data) which would allow the malware creator to reconfigure the mining code.
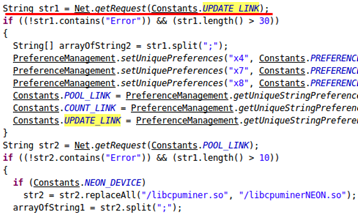
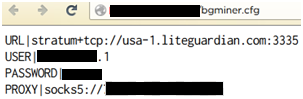
The malware creator apparently earned "thousands of Dogecoins" by the 17th of February, at which point he switched to the WafflePool mining pools (one of which was discovered to be tcp://eu.{BLOCKED}pool.com:3333) by updating the configuration file. Even though mobile devices are rather poor miners, his pool of miners have apparently produced a substantial amount of Bitcoins.
The malware creator recently updated the configuration file again, switching to a Litecoin mining pool - tcp://usa-1.liteguardian.com:3335.
How to fix GDI leaks in Internet Explorer
| If you like this article, please share it! -> |
What Does It Do To My Device?
The affected apps function as they would normally. The only difference is the mining code will make your device work on "mining" cryptocurrencies for its creator. Now, mining cryptocurrencies on a mobile device is a bad idea for various reasons :
-
It puts the CPU under unreasonable load. Mobile phone processors are not expected to run at full load for extended periods of time. Doing so could cause the processor to overheat and malfunction, and reduce its lifespan.
-
It quickly drains battery power because it forces all of the processor's available cores to run at full speed, while transferring data via LTE / 3G or WiFi.
-
The increased thermal load from the processor and wireless chips will likely reduce their lifespans, as well as other components in the immediate area.
-
Mining requires transferring data in and out of the device, which will rapidly eat into one's mobile Internet quota, unless the device is connected to the Internet by WiFi.
In short, this malware is worse than an advertising malware, because it may actually damage your smartphone or tablet.
Your Wireless Mouse Or Keyboard Acting Up? Blame USB 3.0!
| If you like this article, please share it! -> |
How Extensive Is The Problem?
 This malware currently affects only the following Android apps at the moment, but there could be more than have this mining code hidden :
This malware currently affects only the following Android apps at the moment, but there could be more than have this mining code hidden :
- Football Manager Handheld
- TuneIn Radio
- Songs
- Prized - Real Rewards & Prizes
Football Manager Handheld and TuneIn Radio are not served by the Google Play store and appear to use the less sophisticated version of the malware. The mining code launches whenever the affected device is connected to the Internet.
Songs and Prized - Real Rewards & Prizes are in the Google Play store, and appear to use a more sophisticated malware, where the mining code is only activated when the device is charging. This prevents the users from noticing the heat produced by the mining activity and the greatly reduced battery life.
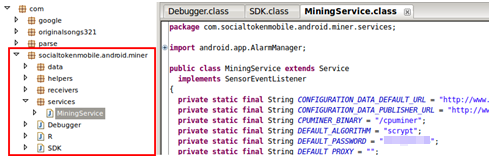
The same miner configuration updating feature is present, and it appears that the malware creator has recently
These apps have been downloaded millions of times, so millions of devices are possibly being misappropriated to mine crytocurrency for the malware creator.
The NVIDIA Control Panel Memory Leak Problem
| If you like this article, please share it! -> |
What Should I Do?
If you own an Android device, make sure the four apps listed above are not installed in your device. If they are, delete them.
There's no way to tell if any of the other apps you have installed are similarly affected but you should be concerned if you notice the following while your device is connected to the Internet :
- your mobile device gets hot even when you aren't doing anything.
- your mobile device's CPU usage is high (if you have an app to monitor it) even when you aren't doing anything.
- your mobile device's battery life is abnormally short.
- your mobile device is taking extraordinarily long to recharge.
- you see a marked increase in your mobile Internet bandwidth usage.
If you notice any of the above, you should try to pinpoint the potentially infected app by removing apps from less trustworthy developers, and see if that changes anything.
If you own an Apple, Windows Phone or Blackberry smartphone, you can breathe a sigh of relief because you are not affected... yet. Laugh at your friends using Android smartphones but remember - this malware can be adapted for other platforms.
Java Plug-In SSV Helper - should it stay or should it go?
| If you like this article, please share it! -> |
Other Scoops
- How To Fix The Apple iCloud Bug (Missing Contacts)
- Big Brother China Censors WeChat... Again
- Intel Haswell Refresh CPU Details Leaked!
- Apple iOS And OS X Have A Critical Security Hole And The Fix Is Here
- Warning - Microsoft Opened A Security Hole In Internet Explorer 11
- How To Fix Keychain Corruption In OS X Mavericks
- AMD's Early 2014 Processor & Graphics Roadmap
- How To Fix Whatsapp Chat History Corruption
If you have a scoop you want to share with us, just contact us! It doesn't have to be Internet-related. It can be anything in the tech industry, from mobile phones to P2P software. Just drop us a message!
Support Tech ARP!
If you like our work, you can help support out work by visiting our sponsors, participate in the Tech ARP Forums, or even donate to our fund. Any help you can render is greatly appreciated!
Support us by buying from Amazon.com! |
|
| Grab a FREE 30-day trial of Amazon Prime for free shipping, instant access to 40,000 movies and TV episodes and the Kindle Owners' Lending Library! | |
Questions & Comments
If you have a question or comment on this editorial, please feel free to post them here!
Date |
Revision |
Revision History |
| 28-03-2014 | 1.0 |
Initial Release. |






 Add to Reddit
Add to Reddit
