ED#185 : The New TrueCrypt - VeraCrypt Or CipherShed?
 Those of you who have been following our coverage of TrueCrypt will remember the uproar when the secretive developers of TrueCrypt mysteriously and unceremoniously pulled the plug on TrueCrypt on the 28th of May, 2014. Many users started panicking, especially when they read the warning that "Using TrueCrypt is not secure as it may contain unfixed security issues".
Those of you who have been following our coverage of TrueCrypt will remember the uproar when the secretive developers of TrueCrypt mysteriously and unceremoniously pulled the plug on TrueCrypt on the 28th of May, 2014. Many users started panicking, especially when they read the warning that "Using TrueCrypt is not secure as it may contain unfixed security issues".
Well, the truth of the matter is TrueCrypt hasn't been updated since February 2012, and is no more vulnerable than it was before they pulled the plug on it. In fact, Phase 1 of the TrueCrypt Audit showed "no evidence of backdoors or otherwise intentionally malicious code".
That said, there is a genuine need for TrueCrypt to be further developed, if only to support newer operating systems and to remove or mitigate the weaknesses identified by the TrueCrypt Audit. Thus, it was no big surprise when everyone started to call for a new team to develop TrueCrypt, or a fork of it.
However, they were soon hit by another bombshell - one of the developers of TrueCrypt announced that they won't agree to an official fork of TrueCrypt. That meant any developer can use the TrueCrypt source code as "reference" but must start their work from scratch. Talk about a WTF moment. That pretty much killed their fanbase at that point.
 In stepped TrueCryptNext (TCNext) - an attempt to kickstart a replacement for TrueCrypt. Despite considerable skepticism, they announced in September that their fledging effort, CipherShed, is now closer to alpha release, pending a security review. This is remarkable progress though, since they only started coding work mid-June. Unfortunate, it has been over a month ago since that announcement, with no updates on the security review.
In stepped TrueCryptNext (TCNext) - an attempt to kickstart a replacement for TrueCrypt. Despite considerable skepticism, they announced in September that their fledging effort, CipherShed, is now closer to alpha release, pending a security review. This is remarkable progress though, since they only started coding work mid-June. Unfortunate, it has been over a month ago since that announcement, with no updates on the security review.
In the meantime, a French cryptography and IT security company called IDRIX announced the release of VeraCrypt 1.0e. VeraCrypt is based on TrueCrypt's source code and looks very similar to TrueCrypt. Take a look at its screenshots :
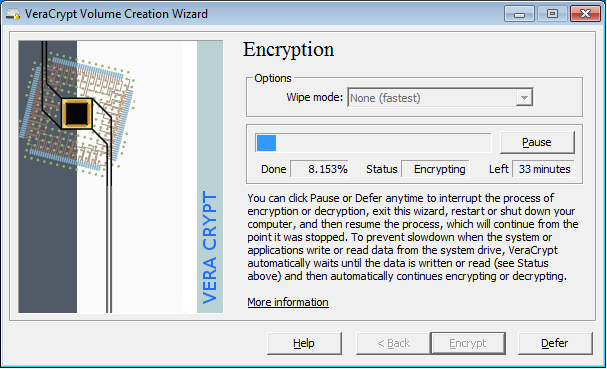
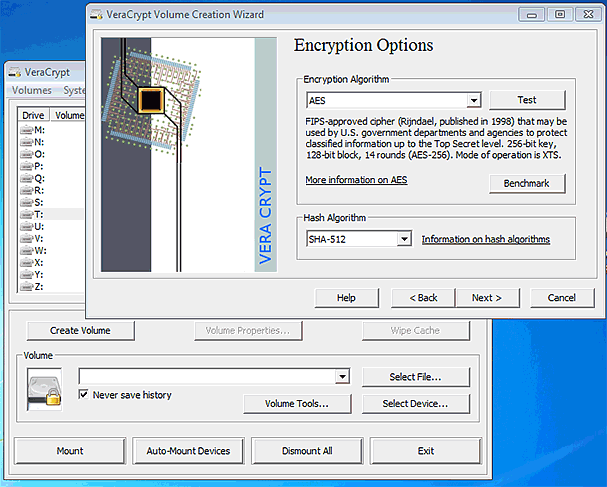
It shouldn't come as a surprise since it appears to be based on TrueCrypt's source code. We are not sure what the TrueCrypt developers would think of their code's use. Of course, IDRIX founder Mournir Idrassi claims that they have greatly improved it by enhancing the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks, as well as solving the many vulnerabilities and security issues found in TrueCrypt :
| VeraCrypt not only enhances security over the original TrueCrypt through an increased iterations count, but it also solves all the serious security issues and weaknesses discovered so far in the source code. A good list of these weaknesses can be found in [this link]. We have documented these security changes in the git commits. The important ones start with "Windows vulnerability fix" and "Static Code Analysis". I'll use the list if the Open Crypto Audit project :
I'm taking this opportunity to announce that we have been able to implement SHA-256 key derivation for system boot encryption (200 000 iterations). TrueCrypt has been always supporting only RIPEMD-160 for system partition encryption and this clearly needed an upgrade because of the aging RIPEMD-160 even if no public attack exists for it. Because of different limitations in the boot loader (code size, memory), this was not an easy task and we had to introduce optimizations and new bootloader management in the VeraCrypt formating program in order to be able to support RIPEMD-160 and SHA-256 at the same time. We'll publish soon a beta version of VeraCrypt 1.0f that will include this SHA-256 in order to have feedback from users. For those who wonder why we implemented SHA-256 and not SHA-512 for the bootloader, the answer is that it was not possible to implement SHA-512 in the 16-bit environment of the bootloader because it needs 64-bit operations which can't be decomposed efficiently into 16-bit operations. On the other hand, SHA-256 uses 32-bit operations which adapts easily to the 16-bit environment even if we lose performance. |
The Tech ARP 2014 Mega Giveaway Contest
| If you like this article, please share it! -> |
Which Should I Migrate To?
Obviously, VeraCrypt is the only viable option if you really want to migrate from TrueCrypt to a free, open-source encryption software. CipherShed is still a work in progress and has not been released even for alpha tests.
Even so, you should really SIT TIGHT and stick with TrueCrypt. For one thing, TrueCrypt 7.1a (the last working release) was independently investigated (by the TrueCrypt Audit) and found to have no obvious backdoors. The same cannot be said for VeraCrypt. We are not disparaging the efforts of the IDRIX team, which we applaud. We are just pointing out a necessary but not always obvious fact.
If you nevertheless feel the need to migrate to VeraCrypt, please note that while VeraCrypt is based on TrueCrypt's code, it uses a different storage format due to the much higher iterations of its cryptographic hash functions. Therefore, you cannot mount your current TrueCrypt containers or partitions using VeraCrypt. You will need to recreate your encrypted containers or partitions using VeraCrypt.
Despite VeraCrypt's early lead, we hope that the CipherShed team will continue with their development. In an ideal situation, we should not have to choose between one of the two. Rather, it would be best if there are two independent open-source solutions. Imagine combining the two - a VeraCrypt-encrypted drive with CipherShed-encrypted containers inside (or vice versa)!
![]() To learn more about the "TrueCrypt crisis", please take a look at our previous articles - The Mystery Of TrueCrypt's Disappearance and TrueCrypt Developer Drops New Bombshell - Open Source Fork "Impossible".
To learn more about the "TrueCrypt crisis", please take a look at our previous articles - The Mystery Of TrueCrypt's Disappearance and TrueCrypt Developer Drops New Bombshell - Open Source Fork "Impossible".
These malware could be using your smartphone to mine cryptocurrencies!
| If you like this article, please share it! -> |
Other Scoops
- #Bendgate Isn't New But It Could Finally Change The Industry For The Better
- The Apple iPhone 6 Isn't The Only Smartphone To Bend It Like Beckham
- Why Are Apple iPhones So Expensive?
- How To Give Adobe Photoshop A Performance Boost
- How To Switch The Location Of The Apple iTunes Backup Folder
- Why It's Really Time To Ditch (And Strip) The Short Filename
- AV-Optimized Hard Disk Drives Are Safe To Use
- TrueCrypt Developer Drops New Bombshell
If you have a scoop you want to share with us, just contact us! It doesn't have to be cryptographic-related. It can be anything in the tech industry, from mobile phones to P2P software. Just drop us a message!
Support Tech ARP!
If you like our work, you can help support out work by visiting our sponsors, participate in the Tech ARP Forums, or even donate to our fund. Any help you can render is greatly appreciated!
Support us by buying from Amazon.com! |
|
| Grab a FREE 30-day trial of Amazon Prime for free shipping, instant access to 40,000 movies and TV episodes and the Kindle Owners' Lending Library! | |
Questions & Comments
If you have a question or comment on this editorial, please feel free to post them here!
Date |
Revision |
Revision History |
| 17-10-2014 | 1.0 |
Initial Release. |







 Add to Reddit
Add to Reddit
