ED#170 : Bitcoin Malware Infects Apple iAd!
![]() The Chinese like to say - "Good things no cheap, and cheap things no good!" and this bit of Oriental wisdom comes true yet again.
The Chinese like to say - "Good things no cheap, and cheap things no good!" and this bit of Oriental wisdom comes true yet again.
Earlier this week, we told you about a new family of Android malware called ANDROIDOS_KAGECOIN.HBT. Most of you pooh-poohed it because :
-
you are using an Apple iPhone, and who has ever heard of a malware on an Apple product? Right???
-
you are using a Windows Phone, and who would bother to make a malware for Windows Phone?
-
you are using a Blackberry, and no one knows Blackberry still exists.

Well, Windows Phone and Blackberry users can continue to cackle your evil laughs. Apple fans, please move over here and stand with Android users, because the same damn malware now infects your devices through Apple's iAd advertising platform!
Just like their Android brethren, the new iOS mining malware hides from detection by appropriating code from legitimate apps. However, the iOS version seems to be the third-generation malware, with stupendous improvements over the two Android versions. If you recall our article on the Android mining malware...
In the Android version, the malware creator took the CPU mining code from Crypto Miner, a legitimate Android cryptocurrency mining app (that was itself based on the open-sourced cpuminer software), and injected it into legitimate apps like Football Manager Handheld and TuneIn Radio. This allowed the malware to appear as functional copies of the real apps, while "mining" cryptocurrencies for the malware creator.
According to Veo Zhang, a Mobile Threat Analyst from Trend Micro, they hid the malicious code by modifying the Google Mobile Ads code :
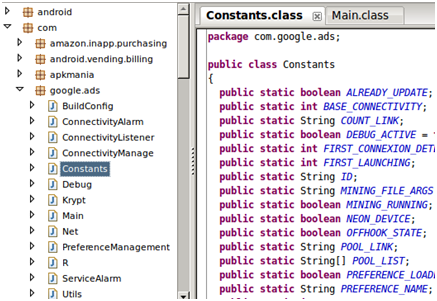
Why we say that the iOS mining malware is smarter and worthy of praise is because it employs code from iOS mining apps like BTC Miner and MobileMiner, which are readily available on the Apple Store. There is even a version that calls the legitimate mining app if it's installed in your iOS device.
In the Android versions, the mining code is activated as a background service when the device connects to the Internet. To evade the strict Apple Store testing requirements, the iOS malware appears to have a delayed mechanism - it only activates a few days after the infected app is first accessed.
Just like in the Android version, the creator used the advertising framework (iAd in this case) to hide and initiate the mining code...
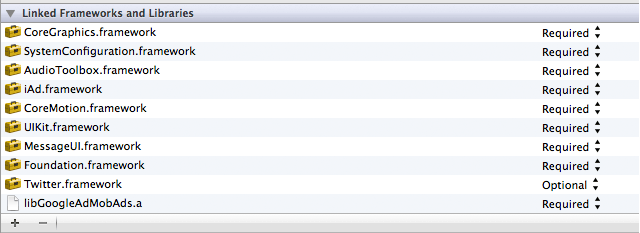
But it's much smarter now - it only runs when your iOS device is connected to an external source of power AND connected to the Internet via WiFi. This way, you wouldn't know that it's running, even if you follow the tips we posted in our article on the Android mining malware.
Smart, right? The malware creator is probably Chinese. The Russians don't have such finesse - look at how they "conquered" Crimea. The Chinese would gotten Crimea with American support, just like Hitler took over Czechoslovakia with England's blessings, but I digress...
Backdoors Found In Bitlocker, FileVault and TrueCrypt?
| If you like this article, please share it! -> |
How Do I Know This Is True?
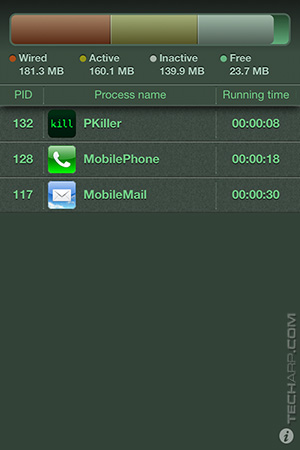
Because I said so? Fine, fine... Take a look at these screenshots of Process Killer. ![]()
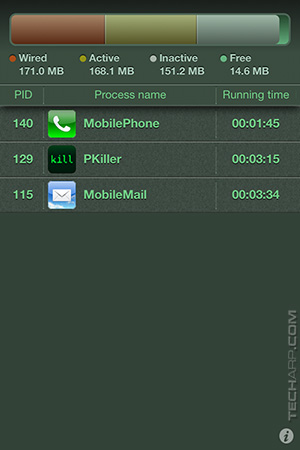 |
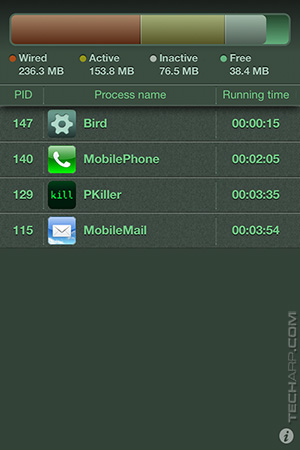 |
After reboot, with 3G enabled. |
After WiFi is enabled. |
Noticed how Flappy Bird mysteriously appeared? Well, you could be thinking - hey, maybe it's just Flappy Bird that's infected? You are quite a distrustful little sod, aren't you? We knew you would think like that, which is why we installed a flashlight app that also runs iAd, and restarted the iPhone.
 |
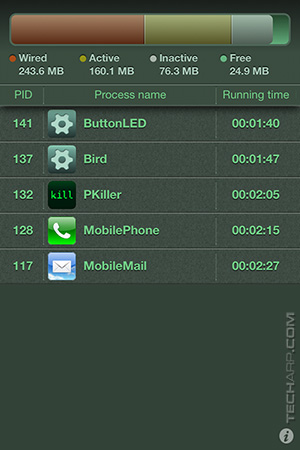 |
After reboot, with 3G enabled. |
After WiFi is enabled. |
See??? Notice how both Flappy Bird and Flashlight started up right after WiFi is enabled, but not with 3G enabled? Now, drop down and give me 20 push-ups!
Spyware In Microsoft Windows 7
I Still Don't Believe You...
As George Bush Jr. once said - "Fool me once, shame on — shame on you. Fool me — you can't get fooled again." Does that make sense?
Never mind. I don't even understand what he meant. You can test it out yourself, if you have Process Killer.
-
Turn off WiFi in your iOS device (iPhone / iPad / iPod touch).
-
Plug your iOS device into an external power source.
-
Restart your iOS device by pressing the Power and Home button until it blanks out and you see the Apple icon.
-
Wait four minutes. That's 240 seconds for you slow pokes.
-
Turn on Process Killer.
-
Wait one minute, or 60 seconds for you slow pokes.
-
Turn on WiFi in your iOS device.
-
Watch as your iOS device enriches a cybercriminal with Bitcoins!
The NVIDIA Ninja Graphics Technology Report
| If you like this article, please share it! -> |
What Should I Do?
My mother always say - "Don't be cheap if you can't be smart about it", and she's absolutely right! 
You cheap sods are in this position because you refused to pay for apps. Paid apps don't have iAd advertisements and are not affected by the malware. But you were both cheap and stupid because you could have gotten the paid apps for free!
If my mother was tech-savvy, she would have taught you to wait for paid apps to become free on AppShopper or AppTicker if you can't help being cheap. Unfortunately, she's not tech-savvy.
Yes, yes, I could have taught you guys how to be smart about being cheap, but I was too engrossed downloading free apps on AppShopper. My bad.
So the moral of today's story is - pay for apps, or use AppShopper... Remember this, if you can remember nothing else from this story - "Don't be cheap if you can't be smart about it!" 
Java Plug-In SSV Helper - should it stay or should it go?
| If you like this article, please share it! -> |
Other Stories
- Backdoors Found In Bitlocker, FileVault and TrueCrypt?
- The NVIDIA Ninja Graphics Technology Report
- Intel's Future SSD Models Leaked!
- Spyware In Microsoft Windows 7
- ATI To Fix Poor Tesselation Performance
- Ray Tracing To Debut In DirectX 11
- NVIDIA GeForce 8800 GTX / GTS' Killer Bug
- NVIDIA Buys Over AGEIA
If you have a story you want to share with us, just contact us! We will give you a free copy of AppShopper for your help. ![]()
Support Tech ARP!
If you like our work, you can help support out work by visiting our sponsors, participate in the Tech ARP Forums, or even donate to our fund. Any help you can render is greatly appreciated!
Support us by buying from Amazon.com! |
|
| Grab a FREE 30-day trial of Amazon Prime for free shipping, instant access to 40,000 movies and TV episodes and the Kindle Owners' Lending Library! | |
Questions & Comments
If you have a question or comment on this editorial, please feel free to post them here!
Date |
Revision |
Revision History |
| 01-04-2014 | 1.0 |
Initial Release. |






 Add to Reddit
Add to Reddit
