"Scan the subspace frequencies for distress signals!" - Captain Janeway
So, now I have a Pocket PC that scans and logs every access point I encounter. What else better to do next than to roam and do some wardriving myself!
The data I gathered were quite eye-opening, to say the least. I won't be publishing the actual tabular data I've gathered, in case someone decides to sue me or Tech ARP. 
![]()
Instead, I've prepared some fancy charts which summarize what I gathered. Let's take a look.
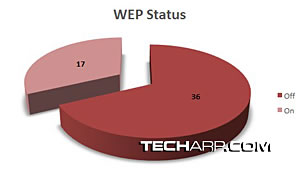
First of all, it was quite shocking to find that more that 68% of the wireless access points that I detected and logged while driving did NOT have WEP turned on! Only 17 out of the 53 networks logged had such protection enabled.
This clearly shows that although many people are beginning set up WiFi networks in their homes, many are still unaware of the security risks that they are exposing themselves to! In fact, on several occasions, I was even able to load up the router's administration console. It wasn't even protected with a custom password!
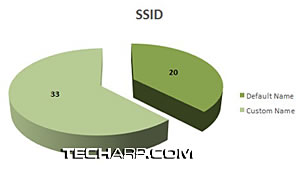
Based on the same logs I gathered, more than half of the access points had custom SSID names. This shows that many of the same users had actually accessed the administration console of their WiFi routers and changed some of the settings.
Yet it astounds me that so many did not bother to setup their router to use at least WEP encryption to protect the network. It appears that many users still relied on the setup wizards that did not required WEP encryption to be set up.
Unfortunately, there are many who actually used the default SSID names. They are either not creative enough to come up with another name, or they are happy campers that their routers were truly "plug and play".
"Analysis, Mr. Spock?" - Captain James T. Kirk
This data clearly shows that many of these tech-savvy users are actually still n00bs (newbies), especially when it comes to network security. They failed to even implement WEP which is frankly not very secure on its own and is definitely hackable.
Still, WEP is still useful as a deterrent against casual leeching by users driving or walking by, hoping to hop onto the Internet for free. While it's not very secure, at the very least, it offers some network security.
As a result of such carelessness, I was able to log myself into the web-based administration console of several routers. Their owners actually left the routers using their default (and totally predictable!) password!
All I had to do was to connect to the unsecured access point and automatically obtain an IP via DHCP. Then based on the IP settings, I tried loading the gateway IP on my browser. Sure enough, I gained access to the router's login screen.
What's next? I figured that if they kept the default SSID name, it was very likely that the password was still the default one as well. Even if I cannot guess the correct password, all I had to do was Google for the default password of the router. Remember, at this point, I was already connected to the Internet.
If I wanted to actually do some damage, I could just simply look into the DHCP settings in the router's administration console and get information on any device that was hooked onto the network and attempt to penetrate based on that information.
Of course, I didn't go any further. My whole point was just to test how easy it was to break into wireless networks.
<<< Dude, Where Is Your WEP?, "Captain! The Tricorder Isn't Listening To Me!" : Previous Page | Next Page : "Fate Protects Fools, Little Children, And Ships Named Enterprise.", Endgame >>>






 Add to Reddit
Add to Reddit