Diagnosing The Problem
Scanning with a spyware scanner is a good way to start, but I'll show you the good, old manual ways so you can get a good understanding of what to look for when it comes to securing your PC. Another reason why learning basic diagnosis techniques is a good thing is because you may not have all the tools you need for detection are available to you at all times, and sometimes going manual is the only way you'll get anything done quickly.
Of course, these aren't super diagnostic programs or anything. It's just like how a doctor diagnoses a patient. He can't tell if the man is sick just by using a stethoscope, can he? He'll have to use a variety of tools to diagnose the patient, just like what you'll be doing in a while.
Another reason why you should look into this section is that knowledge here allows you to kill off problems, be it spyware, viruses and trojans without relying too much on third party programs. With these simple techniques, you can easily hunt down most offending programs and push the Del key on them, sending them on a one-way trip to hell.
Don't worry, my friends. It isn't as hard as medicine. Just follow my tips and you'll be fine.
Netstat
 |
Shut down as many of your software that uses the Internet (like web browsers, e-mail clients, P2P clients, FTP clients, etc.).
Then click Start Menu -> Run. Type “cmd” and press Enter. This opens up the Command Prompt, which looks like a small black box.
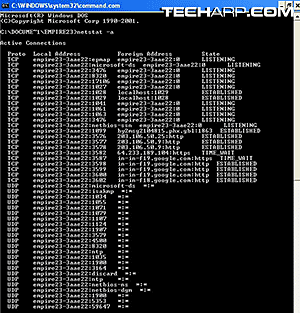
Type in “netstat -a” at the prompt and press Enter. This should result in a long list like in the picture on the right.
The text looks like Greek and doesn't make any sense to you? Well, while it looks really complex, you don't really need to know anything more than the number of text lines there are in the above.
When used for the usual web surfing activities, most PCs should have a list just like that, with about 20-40 connections. Of course, if you're downloading a ton of stuff, you will see even more connections.
However, if you close most or all of your network accessing software and still get a list of a few hundred connections, then something is seriously wrong. It means that something is opening all those connections behind your back. That usually implies a hijack. It's not a solid sign that you have been hijacked, but at least you have just sniffed out a possible problem.
MSConfig
 |
Now, click Start Menu -> Run again. But instead of entering “cmd” in the Run box, type “msconfig” instead and then click “OK”.
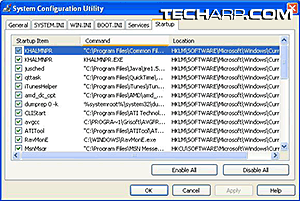
You would be greeted with the System Configuration Utility. Head for the the Startup tab, because most spyware and some trojans add a registry string to the Windows registry that commands Windows to start them up every time the PC is started up.
Of course, there are other parts of the System Configuration Utility that can be used to hunt down invaders, but this is the simplest way and to be honest with you, it catches 90 percent of the offenders.
Now, all you need to do now is scan the list for programs that you did not install. The simplest way to do that would be to identify legit programs. For example, MsnMsgr is a legitimate software because it is the MSN Messenger is an instant messenger that is installed by default in most Windows XP systems.
Generally, you need a little common sense to do this. If you did not intentionally install something like XXX Dialer, it really should not be there in the list. Also, if you see a startup item with a legitimate name but with a suspicious location, it could be a trojan masquerading as a legit program.
So, using MSConfig to hunt down invaders is a skill that depends on your grasp of the software you have installed, and some common sense. My rule of thumb is, if it shouldn't be there, it's probably not good.
<<< Pinpointing The Threat - Hijacking, Spying, Generally Annoying The Heck Out Of You : Previous Page | Next Page : Task Manager, Windows Event Viewer >>>






 Add to Reddit
Add to Reddit
